Security Layers
The security of data is paramount, and data is money. There are seven layers of security, with data at the core. The innermost layer has more value than the outer layer. Accessibility decreases as you travel to the innermost layer.
Figure 6-8 demonstrates the seven layers of security: (1) human layer, (2) physical parameter layer, (3) access point/end point, (4) network layer, (5) infrastructure layer, (6) application layer, and (7) data layer.
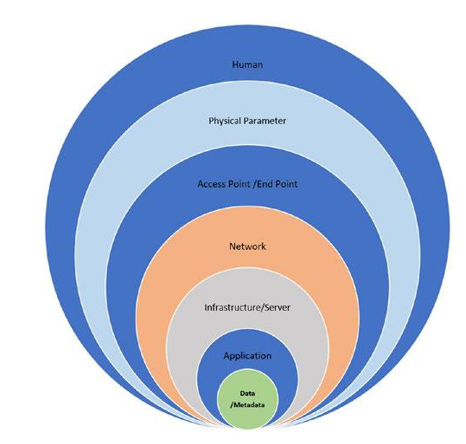
Figure 6-8. Seven layers of security
“Data is money.” Data is the center of all security, and the purpose of security is to save data.
Understanding the different layers helps in safeguarding your company’s reputation in terms of managing customer data. This knowledge says that client-facing portals should be reliable, compliant to regulations, and safe to use. It is essential to safeguard the company’s reputation by saving the data.
Human Layer
Once a device is compromised, cybercriminal hackers may gain access to your partial or entire network. People can be the weakest link in the organization’s information security program.
Out of the seven layers, the human layer is the first line of defense. Employees, contractors, external partners, and business vendors make up this layer. The human layer is the outermost layer of security in terms of having the most vulnerability in security. Thirty-two percent of breaches are caused by phishing attacks, and malware delivered through emails is one of the major reported incidents. Hackers use social engineering frequently to manipulate the users or stakeholders to obtain access to information about a system.
The human layer is more vulnerable than the non-human layer in IT security. This vulnerability can be reduced substantially by increasing proactiveness. The goal of actions is to increase the degree of proactiveness in IT security at this layer. Some of the ways to reduce vulnerability are as follows:
• Regular and mandatory awareness training of all stakeholders.
Making sure that all stakeholders understand their role and actions in case of attack
• Creating tools and technology components as part of an IT security program
• Increasing the technical skills of non-technical employees,contractors, and vendors; e.g., training to prevent non-technical staff from clicking on suspicious emails and links. Increasing awareness through training and education to spot phishing attacks
• Creating policies, procedures, and awareness—and subsequently implementation of training.
